A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a network, service, or website by overwhelming it with a flood of internet traffic. These attacks are carried out by multiple compromised computers and can cause significant disruption. If you are using Cloudflare service and you are under a DDoS attack, immediately enable “HTTP DDoS attack protection” and also the “I’m under attack” option.
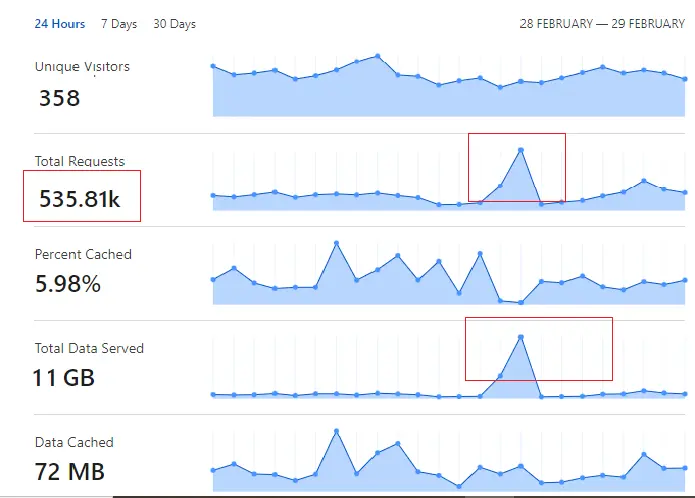
How to Stop a DDoS Attack
Stopping a DDoS attack involves several steps:
- Block the DDoS Attack: The first step is to try to block the attack. This might require outside assistance or even shutting down the resource temporarily.
- Determine the Type of DDoS Attack: Analyze log files, alerts, and other records for clues about the source and type of DDoS attack.
- Recover from the DDoS Attack: Change your security architecture, processes, or tools to recover from the current attack and prevent further attacks.
How to Detect a DDoS Attack
Detecting a DDoS attack involves observing certain parameters, as noted below:

- Unusual Increase in Traffic: A sudden, significant increase in traffic can be a sign of a DDoS attack.
- Server Responds with a 503 Error: If your server is responding with a Service Unavailable or HTTP error 503 message, it could be due to a DDoS attack.
- Ping Requests Time Out: If your ping requests are timing out, this could be another sign of a DDoS attack.
- Multiple Requests from the Same IP Address: Receiving multiple requests from the same IP address or range of IP addresses can be a sign of a DDoS attack.
- Spike in Bandwidth Usage: A sudden spike in bandwidth usage can also indicate a DDoS attack.
How to Prevent DDoS Attacks
Preventing DDoS attacks involves several strategies:
- Set up a WAF: A Web Access Firewall (WAF) can help protect your website from DDoS attacks by filtering out malicious traffic.
- Country Blocking: If you notice that a lot of malicious traffic is coming from a specific country, you can block traffic from that country.
- Monitor Web Traffic: Regularly monitoring your web traffic can help you identify unusual patterns that might indicate a DDoS attack.
- Increase Bandwidth: Having extra bandwidth can help your website absorb the increased traffic that comes with a DDoS attack.
- Move to the Cloud: Cloud-based services can often handle larger traffic volumes and are typically more resilient to DDoS attacks.
- Implement Rate-Limiting: Rate limiting can help prevent a DDoS attack by limiting the number of requests a user can make within a certain time period.
- Set up Caching: Caching can help reduce the impact of a DDoS attack by serving static versions of your web pages.
How Cloudflare Helps Prevent DDoS Attacks
Cloudflare provides several methods to help prevent DDoS attacks:
- Attack Surface Reduction: Cloudflare helps to minimize the effect of a DDoS attack by limiting attack surface exposure. This includes restricting traffic to specific locations, implementing a load balancer, and blocking communication from outdated or unused ports, protocols, and applications.
- Anycast Network Diffusion: An Anycast network increases the surface area of an organization’s network, so it can more easily absorb volumetric traffic spikes (and prevent outages) by dispersing traffic across multiple distributed servers.
- Real-Time, Adaptive Threat Monitoring: Cloudflare provides log monitoring that can help pinpoint potential threats by analyzing network traffic patterns, monitoring traffic spikes or other unusual activity, and adapting to defend against anomalous or malicious requests, protocols, and IP blocks.
- Integrated L3-7 DDoS Protection: Cloudflare offers integrated L3-7 DDoS protection that helps organizations monitor, prevent, and mitigate attacks before they reach targeted applications, networks, and infrastructure.
- Autonomous DDoS Systems: Cloudflare’s autonomous edge and centralized DDoS systems analyze traffic samples out of path, which allows Cloudflare to asynchronously detect DDoS attacks without causing latency or impacting performance.
Custom WAF Rules in Cloudflare
In Cloudflare’s WAF, you can create custom rules using the Expression Preview feature to fine-tune your security policies. Here are five custom WAF rules you can set up using Expression Preview to help stop DDoS attacks:
- Rate Limiting on Specific Endpoints:
when http.request.uri.path matches "^/critical_endpoint" { throttle by ip(1000, 60 seconds); }- Request Method Filtering:
when http.request.method ne "GET" and http.request.method ne "POST" {
deny;
}- HTTP Header Validation:
when not http.request.headers["User-Agent"] or http.request.headers["User-Agent"] contains "Mozilla" {
deny;
}- Rate Limiting on Origin Server Requests:
when true {
throttle by request.ip(100, 5 seconds);
}- Dynamic IP Blocking:
when cf.threat_score ge 50 {
block;
}These custom rules leverage the capabilities of Cloudflare’s WAF and Expression Preview to implement targeted protections against DDoS attacks. Make sure to adjust the parameters and conditions based on your specific security requirements and traffic patterns.
Comparison of DDoS Protection Providers
Cloudflare is often recognized as one of the top providers for DDoS protection. Here’s how it compares to other providers:
- Cloudflare: Known for its cloud-based DDoS protection system, Cloudflare can handle Layer 7 attacks as well as Layer 3 and Layer 4 attacks. It has a free plan that provides basic DDoS protection and CDN, as well as paid plans that offer more features and support. The pro plan starts at $20 per month per domain.
- Radware: Radware offers tailored, scalable DDoS protection solutions. It also provides other services, such as load balancing, application delivery, and bot management. Radware’s pricing depends on the customer’s needs and the level of protection required. It starts from $16,000 in the marketplace.
- Imperva: Imperva provides instant, high-capacity DDoS mitigation. It uses a cloud-based platform that can automatically detect and block DDoS attacks within seconds, as well as a network of data centers that can handle up to 3 Tbps of traffic. Imperva also offers other services, such as WAF, CDN, and API security.
- Amazon Web Services (AWS): AWS offers scalable protection on AWS infrastructure. AWS Shield’s pricing is based on the customer’s usage of AWS resources and the level of protection selected. The standard tier is free, while the advanced tier costs $3,000 per organization per month.
- Akamai: Akamai offers defense against application threats. It uses a cloud-based platform that leverages its global CDN network to filter and mitigate DDoS attacks, as well as a suite of tools and services, such as Kona Site Defender, Prolexic Routed, and Fast DNS.
Understanding Layer 3, Layer 4, and Layer 7 Attacks
Layer 3, Layer 4, and Layer 7 refer to different layers of the OSI (Open Systems Interconnection) model, and each can be targeted by different types of DDoS attacks:
- Layer 3 – Network Layer Attacks: This layer is where IP (Internet Protocol) communication occurs, involving the routing of packets between source and destination networks. Layer 3 is vulnerable to attacks such as IP spoofing and Smurf attacks.
- Layer 4 – Transport Layer Attacks: This layer handles the transmission of data between systems and hosts, and includes protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Layer 4 attacks often involve SYN floods, where the attacker initiates a connection with the target but never completes the handshake, leaving the connection in a half-open state and consuming resources.
- Layer 7 – Application Layer Attacks: This is the layer where HTTP requests occur, and it involves the communication that happens when users try to access a specific service, like a webpage. Layer 7 attacks often involve HTTP floods, where the attacker overwhelms the target with HTTP requests.
Conclusion
DDoS attacks can cause significant disruption and damage, but with the right strategies and tools, you can protect your network and keep your services running smoothly. Whether you’re a small business owner or a network administrator for a large corporation, understanding DDoS attacks and how to prevent them is crucial for maintaining the security and integrity of your digital assets.
Learn More | How to stop DDoS attack
Cloudflare Bot Fight Mode: Whitelist Good Bots and Block Bad Bots

