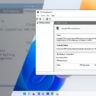
If you’re seeing the Azure Policy error “Enable MFA for tenant before October 2025”, it means your organization has not yet enforced Multi-Factor Authentication (MFA) for users who perform Azure management tasks. Microsoft is rolling out mandatory MFA enforcement in phases, and from October 1, 2025, all Create/Update/Delete operations via Azure CLI, PowerShell, REST APIs, and infrastructure tools will require MFA.
Microsoft is phasing in MFA requirements to strengthen account security across Azure and Entra ID.
- Phase 1 (2024 – early 2025): MFA required for signing into Azure Portal, Entra admin center, and Intune.
- Phase 2 (from October 1, 2025): MFA required for resource-management actions via Azure CLI, Azure PowerShell, REST APIs, and IaC tools.
If your tenant does not meet the requirement, management operations will fail until MFA is enabled.
How to Fix the MFA Tenant Requirement
1. Enable Security Defaults (Fastest Option)
If you’re using Entra ID Free, turning on Security Defaults automatically enforces MFA for all admins and users.
- Go to Entra ID → Properties → Manage security defaults.
- Set Enable security defaults = Yes.
This ensures compliance without creating custom Conditional Access rules.
2. Create a Conditional Access Policy (Recommended)
For most organizations, Conditional Access (CA) gives more flexibility than Security Defaults.
Steps:
- Open Entra ID → Protection → Conditional Access → New policy.
- Assignments:
- Users → Directory roles → All administrators.
- Later, include groups that manage Azure resources.
- Target cloud apps: Select Microsoft Azure Management.
- Access controls: Require MFA.
- Exclude break-glass emergency accounts.
- Start in Report-only mode → switch to On after testing.
This ensures MFA enforcement for all management activity across CLI, PowerShell, and portal.
3. Audit with Azure Policy Before Enforcing
Microsoft provides built-in Azure Policies to audit whether MFA is applied to management actions.
- Assign the policy in Audit mode first.
- Review compliance reports.
- Switch to Deny mode once confident.
This reduces the risk of unexpected failures in pipelines or automation scripts.
Tooling & Client Updates Required
For MFA enforcement to work, users must upgrade their tools:
- Azure CLI ≥ 2.76
- Azure PowerShell ≥ 14.3
Older versions may not support MFA prompts correctly and can break automation.
What If You Can’t Finish Before October 2025?
If your organization needs more time, a Global Administrator can temporarily postpone MFA enforcement in the Azure portal. Keep in mind this is only a short-term workaround and should not replace a proper rollout.
To prepare effectively and avoid last-minute issues, follow these best practices:
- Roll out MFA gradually using Conditional Access in report-only mode.
- Train users on supported MFA methods (Authenticator app, FIDO2 keys, SMS as backup).
- Keep at least one break-glass account without MFA, but secure it with strong controls.
- Monitor compliance regularly through Azure Policy reports.
- Update DevOps agents, scripts, and pipelines to ensure MFA compatibility before Oct 2025.
The “Enable MFA for tenant before October 2025” error is Microsoft’s way of warning you to act before enforcement kicks in. By enabling Security Defaults or deploying a Conditional Access MFA policy, you’ll secure your tenant, avoid service disruptions, and stay compliant with Microsoft’s new security requirements.